Basic steps (all client programs)
Use Windows users with AD
Milestone recommends that, whenever possible, you use Windows users in combination with Active Directory (AD) to log in to the VMS with the client programs. This enables you to enforce a password policy, and apply user settings consistently across the domain and network. It also provides protection against brute force attacks. For more information, see Use Windows users with Active Directory.
Learn more
The following control(s) provide additional guidance:
- NIST 800-53 CM-6 Configuration Settings
- NIST 800-53 SA-5 Information System Documentation
- NIST 800-53 SA-13 Trustworthiness
Restrict permissions for client users
Milestone recommends that administrators specify what users can do in Management Client or XProtect Smart Client.
The following instructions describe how to do this. Additional information is available in the Advanced Security Management white paper.
To restrict client user permissions, follow these steps:
- Open Management Client.
- Expand the Security node, select Roles, and then select the role that the user is associated with.
- On the tabs at the bottom, you can set permissions and restrictions for the role.
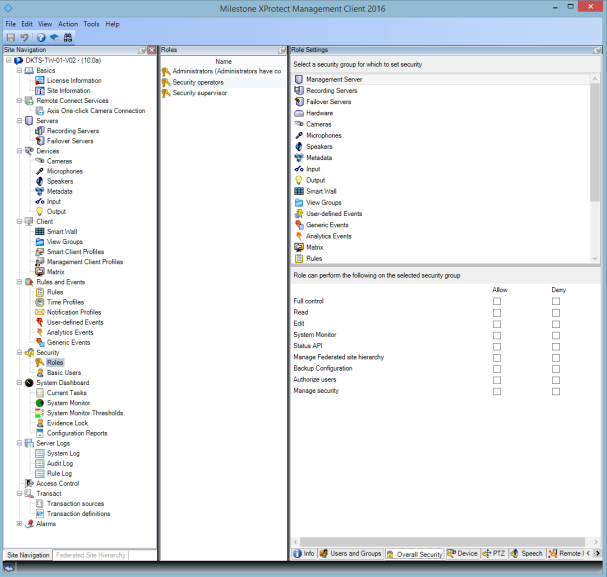
By default, all users associated with the Administrator role have unrestricted access to the system. This includes users who are associated with the Administrator role in AD as well as those with the role of administrator on the management server.
Learn more
The following documents provide additional information:
- NIST 800-53 AC-4 Least Privilege
- NIST 800-53 CM-6 Configuration Settings
- NIST 800-53 CM-7 Least Functionality
Always run clients on trusted hardware on trusted networks
Milestone recommends that you always run XProtect clients on hardware devices with the proper security settings. Specific guidance for mobile devices is available in SP 800-124 (https://csrc.nist.gov/publications/detail/sp/800-124/rev-1/final). These settings are specific to the device.
Learn more
The following control(s) provide additional guidance:
- NIST SP 800-53 SC-7 Boundary Protection
- NIST SP800-53 CM-6 Configuration Settings

