Deployment Considerations
Selecting EC2 instance type
One of the greatest advantages of deploying XProtect on an elastically scalable cloud infrastructure is the possibility to freely select the configuration of the compute infrastructure at the system design point, and the ability to dynamically resize that platform as needs and operational conditions change. AWS offers a wide set of EC2 instance types that makes it possible to continuously optimize the compute infrastructure, to obtain the best possible performance and cost ratio.
Prior to the publication of the XProtect on AWS Marketplace, Milestone has conducted extensive system performance tests to short list a set of EC2 instances recommended for XProtect VMS deployments. This has resulted in seven EC2 instances offering the most advantageous cost per connected camera across the range of 10 to 500 cameras per XProtect recording server.
|
INSTANCE FAMILY |
DESCRIPTION |
INSTANCE TYPE |
|
T3 |
Burstable general-purpose instance type |
t3.large |
|
C5 |
Optimized for compute-intensive workloads |
c5.large c5.xlarge c5.2xlarge |
|
G4 |
Optimized for graphics-intensive workloads Include NVIDIA T4 Tensor Core GPUs |
g4dn.xlarge g4dn.2xlarge g4dn.4xlarge |
Table 1. Recommended EC2 instance types for XProtect BYOL
Appendix C – EC2 performance presents the recommended EC2 instances and the performance metrics measured for these instance types.
On-premises – AWS cloud connectivity
The customer’s on-premises environment(s) with camera assets and client applications need to be connected to the XProtect VPC using standard AWS networking services such as AWS Site-to-Site VPN and Direct Connect, or similar third-party networking technologies. This section discusses how AWS Site-to-Site VPN service can be applied to an XProtect deployment. For more advance methods using AWS Direct Connect, or AWS Transit Gateway, please refer to AWS documentation.
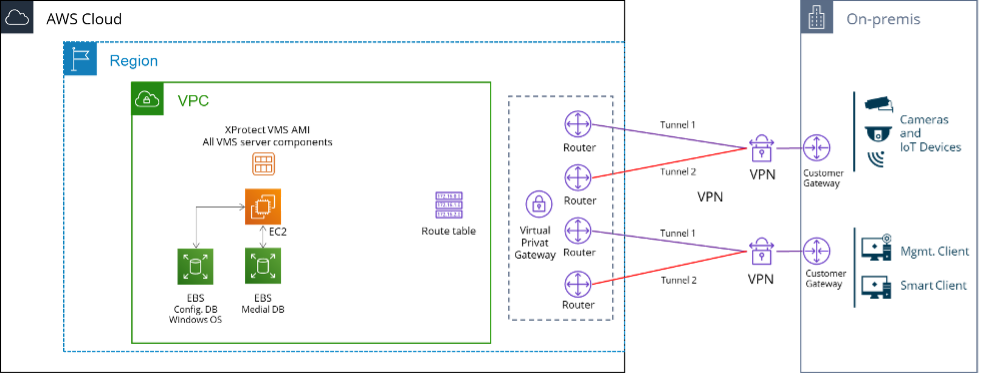
Figure 6. Principal design of a redundant Site-to-Site VPN topology for a single site deployment
Designing the network topology connecting the customer site(s), one should consider required bandwidth for video streams and client access, and factor in peak situations and the need for redundancy. Figure 6 presents a principal redundant VPN design for a single site deployment. It should be noted that each VPN connection is made up by two separate IPsec tunnels, which represent the first level of redundancy in the event of a device failure within AWS. Second level redundancy is achieved by the two separate VPN connections, each handled by its dedicated customer gateway device. It is further recommended that these two VPN connections are routed via two different Internet Service Providers to ensure maximal redundancy. The VPN gateway that facilitates the Site-to-Site connectivity is attached to the XProtect VPC via the routing table.
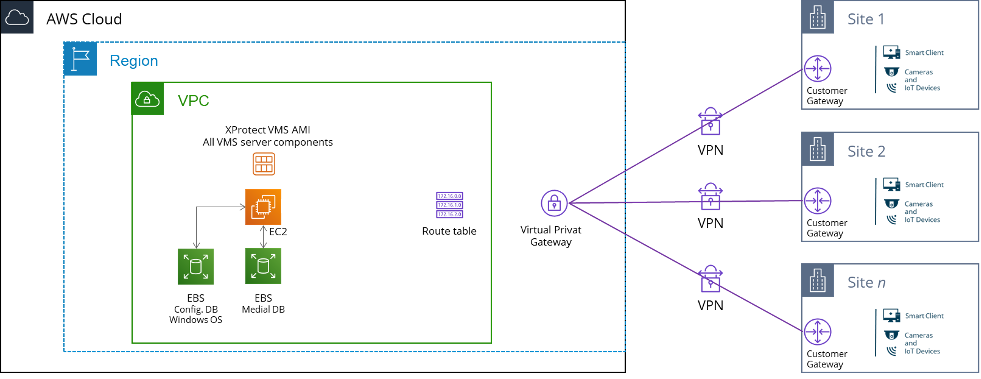
Figure 7. Example of a multi-site deployment using AWS Site-to-Site VPN
Enterprises and organizations often have geographically dispersed facilities and offices, where the security operation is to be coordinated in one centrally managed video management system. To support this, the individual sites can be connected to the XProtect VPC using the AWS Site-to-Site VPN service, as illustrated in Figure 7. Please note that the figure does not consider redundancy in the VPN topology.
In larger deployments it is important to consider that the maximum throughput of an individual VPN tunnel is 1,25 Gbps, and that the Virtual Private Gateway are bound by an aggregate throughput limit from AWS to on-premises of up to 1,25 Gbps. For AWS Direct Connect connection on a Virtual Private Gateway, the throughput is bound by the Direct Connect physical port itself. To connect to multiple VPCs and achieve higher throughput limits, use AWS Transit Gateway.
The AWS Transit Gateway connects to the customer’s on-premises environment using the same VPN mechanisms as the Virtual Private Gateway. This white paper will not cover designs including the Transit Gateway further. Instead system integrators and end customers are advised to study AWS documentation on the Transit Gateway (see: https://docs.aws.amazon.com/vpc/latest/tgw/what-is-transit-gateway.html). While designing the VPN infrastructure system, integrators should also consider AWS Site-to-Site VPN quotas, which can be increased upon request: https://docs.aws.amazon.com/vpn/latest/s2svpn/vpn-limits.html
Please note that customer gateway devices used with both the VPN Gateway and the Transit Gateway must support the Internet Key Exchange (IKE) protocol, which is used to exchange keys during the establishment of the IPsec security association. AWS also requires special configuration of the customer gateway devices. For more information and a list of tested customer gateway devices, please refer to AWS Site-to-Site VPN user guide (https://docs.aws.amazon.com/vpn/latest/s2svpn/VPC_VPN.html).
Media storage
The XProtect recording server operates with a tiered storage architecture made up by a media database and one, or more, levels of archives, which enables optimization of system performance and storage costs. Media archived to an archive storage remains on-line and is seamlessly accessible for navigation and playback by any client application. Please see the XProtect Storage Architecture and Recommendations white paper for complete information around media storage in XProtect.
There are two approaches possible for archiving:
-
Using another archive storage: In deployments where video is to be retained for longer than just a few days and another file storage is preferred for archiving, Milestone recommends the use of a two-tiered storage with the short-term storage (media database) and long-term archive storage.
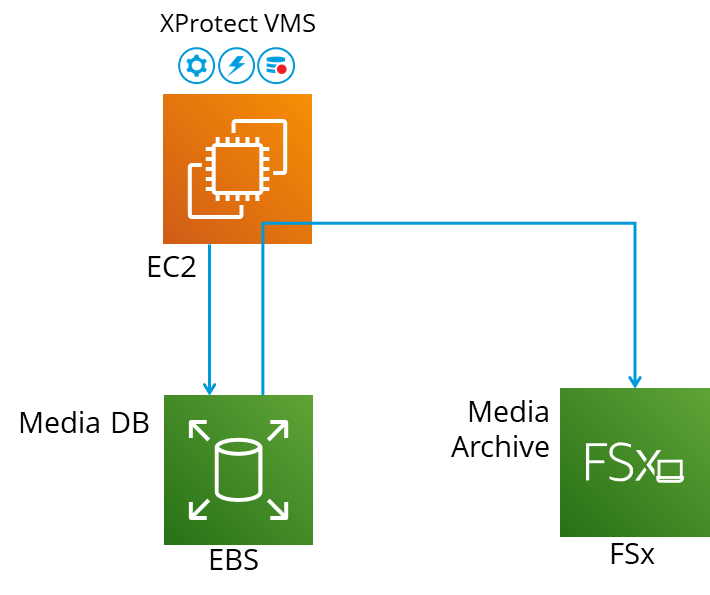
Figure 8. XProtect media storage utilizes a combination of EBS and FSx storage for optimal combination of storage performance and cost
Figure 8 depicts the recommended storage infrastructure when running XProtect on AWS without any third party plugin or add-on that facilitates archiving, where the recording server’s media database is hosted in an EBS general purpose SSD (gp2) storage volume and the media archives are stored in one of more Amazon FSx for Windows File Server storage volumes, dependent on the amount of video and other media data that is to be stored. In this setup the native XProtect video archiving function is used to move, and life cycle manage the video across the EBS and the FSx storage arrays.
The default deployment of XProtect BYOL CloudFormation configures the Elastic Block Store (EBS) for the media database only. This means that the FSx storage shall be added to the installation when and as needed. The FSx storage is available in single-AZ and multi-AZ deployment options, which offers an additional level of redundancy for end-customers with high demands on data resilience. Also, another option for storage is S3 as now the option is provided in the CloudFormation Template.
It is possible to use S3 with provided plugin. In that case, using Archiving is not needed, instead that task can be handled through Surveillance Bridge plugin. It is possible to configure movement of data into various storage options. In case user does not want to use S3 or use the plugin, to obtain maximum system performance while keeping the AWS service costs to a minimum, Milestone recommends keeping minimum amount of video (normally around 24 hours of recordings) in the EBS based media database, with frequent archiving to the long-term FSx HDD based storage. The overall performance of the combined EBS and FSx storage infrastructure is constrained by baseline bandwidth and IOPS allocations for not only the EBS and FSx storages, but also the specific EC2 instance used. It is therefore important to consider the combined performance of all these three elements, when dimensioning the storage infrastructure. Appendix D – Media storage dimensioning details the specific dimensioning considerations.
Please note that FSx requires an active directory (AD) to be defined. The XProtect VPC should therefore be connected to an AD before the FSx storage is defined.
-
Milestone XProtect on AWS CloudFormation template also supports third-party plugin or add-on Surveillance Bridge from Tiger Surveillance. Using that plugin enables archiving to be handled by the mentioned plugin. Refer to Appendix for more information.
Alternative storage options
AWS offers a wide range of storage services, where Milestone recommends S3 in case user wishes to use third party plugins or FSx for long term media storage in case no third party plugin is to be used. So viable options are: AWS S3 or AWS FSx or AWS EBS.
An additional option to the EBS storage that the CloudFormation template defines for the media database is to define a second EBS storage for archiving. The block storage should be throughput optimized HDD (st1) volumes and could be particularly relevant for deployments with shorter retention times (less than 1 week), cf. Appendix D – Media storage dimensioning.
The AWS Simple Storage Service (S3) can be used as an alternative or complement to the FSx based archive storage. The S3 storage can be particularly relevant when on-premises recording servers are configured to archive to an AWS cloud storage. The XProtect recording server does not integrate natively with the S3 object storage through its storage APIs. Therefore, a separate AWS Storage Gateway service needs to represent the object storage bucket as an addressable network drive for the VMS software. Furthermore, Surveillance Bridge can be utilized as well for using S3 for archiving (or as main Media Database). Dependent on the retention time and access patterns to recorded video data, customers can optimize their storage costs by selecting the most optimal S3 storage class.
Use of camera-based edge storage
It is sometimes difficult to obtain a satisfactory level of reliability and redundancy in the interconnecting VPN topology between the AWS cloud and the customers various sites. There are many reasons for this, including general regional scarcity of high-speed internet connectivity, high connectivity costs or technical limitations. In these cases, Milestone recommends the use of camera-based edge storage.
The use of camera-based storage is an ideal solution as it ensures that video and other data is continuously recorded even in the event of shorter interruptions in the connectivity between the customer’s on-premises environment and AWS cloud environment. Once the connection is restored, recordings will be automatically transferred to the XProtect recording server in the AWS cloud, thus ensuring continuous recording of video despite possible intermissions in the connectivity.
For details about the use of edge storage, please refer to the Edge Storage with flexible retrieval white paper.
Data Protection
Video surveillance data is sensitive data that need to be protected from unauthorized access and use. Unlike a Software as a Service (SaaS) offering, in which the customer has no or little control over where the applications run and data is stored, XProtect on AWS puts the customer in full control of where the video data is stored and how it is protected. That means, no video data leaves the specific AWS data center (Availability Zone) in which the XProtect VMS is deployed at, unless otherwise is configured specifically in the actual customer architecture.
SQL Database
The XProtect VMS system stores and maintains all its configurations, event data and logs in Microsoft SQL databases. As a part of the deployment of the XProtect BYOL CloudFormation, a local Microsoft SQL Express database is installed in the EC2 instance. This database is configured as the default SQL database for the vital XProtect VMS system data. This database shall be backed up and managed manually. In larger installation, where a dedicated SQL server may exist, the XProtect system can be configured to use a separate EC2 instance to host a dedicated SQL server.
Another option is using Amazon RDS for SQL Database. This is supported by XProtect as well. Milestone is planning to provide option for using Amazon RDS for SQL Database through CloudFormation template in future.
Deployment instructions
System integrators and end-customers considering a deployment of XProtect on AWS are advised to study eLearning courses and deployment guides provided by Milestone. The material is published on the Milestone website, and available as a part of the XProtect BYOL listing in AWS Marketplace.
e-Learning courses:

