VMS roles and external IDP users
Users from the external IDP cannot be added to the XProtect VMS roles in the same way as Microsoft Active Directory (AD) users, local Windows users, or XProtect VMS basic users.
With the standard AD users or local Windows users, the AD or the local Windows computer can be queried for groups and users, that then can be selected and added to the roles in question. With XProtect VMS basic users, the basic user can be manually created directly in the XProtect VMS and added to the roles.
When using external IDPs, the XProtect VMS cannot query the external IDP to read groups or users. Instead, the XProtect VMS automatically creates the external IDP users in the XProtect VMS and link them to roles based on claims provided to the users by the external IDP. Alternatively, in cases where claims related to the XProtect VMS roles are not provided to the external IDP users, the external IDP users are created in the XProtect VMS upon their first login, but they are not linked to any of the roles. The XProtect VMS administrator must manually add these users to the roles.
Claim-based XProtect VMS role linking
To automatically link the external IDP users to the XProtect VMS roles, the external IDP users must have XProtect VMS role-related claims defined. These claims are included in the users’ ID token from the external IDP and are then used to link the external IDP users to the defined XProtect VMS roles.
To understand how external IDP claims can be used to link the external IDP users to the roles, it is important to know that the external IDP claims consist of a claim name and a value. For example:
-
Claim name = “security_access_type”
-
Claim value = “operator” (or = “admin”, or = guard”, etc.)
To configure the XProtect VMS with the claims to look for and parse, the claims must be registered for the external IDP provider. This is done in the dialog where the external IDP is also defined.
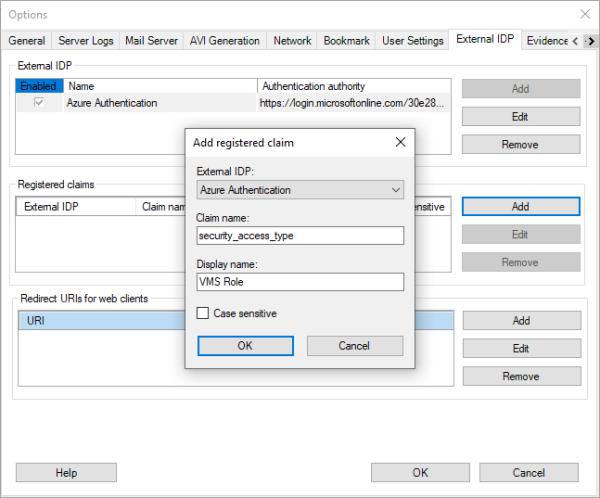
When registering a claim in the XProtect VMS, the claim name defined in the external IDP must be entered exactly as defined in the external IDP. Secondly, a display name for the claim to be used in the XProtect VMS roles dialog must also be entered.
For example, as shown in the screenshot.
-
‘Claim name’ = “security_access_type” (As defined in the external IDP)
-
‘Display name’ = “VMS Role” (For usage in the XProtect VMS roles)
The XProtect VMS will now parse the users’ ID token. If their claim value matches the ones set for the roles, the external IDP users are linked to the XProtect VMS roles.
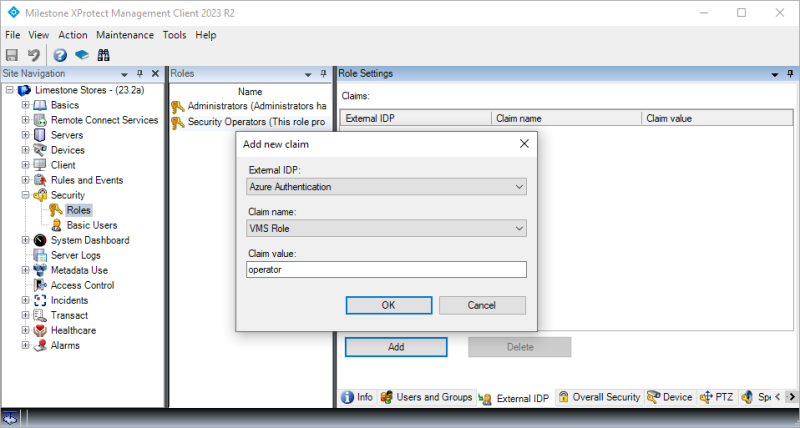
The next step is to configure the claim(s) and value(s) that should link the external IDP user to the individual XProtect VMS roles. This is done by selecting a role, and on the ‘External IDP’ tab, add claims.
In the dialog’s ‘Claim name’ field, select what registered claim to parse. Then enter the claim value that will be used to link users to this role.
The use of the claims and their values in the roles is very flexible. When using claims and values in the roles, it is, for example, possible to:
-
Use multiple claims in a single role using the same claim name, but with different values
-
Use multiple claims in a single role using different claim names and values
-
Use the same claims in multiple roles using the same claim name and values
-
Use the same claims in multiple roles using the same claim name and different values for each role
When external IDP users log in to the XProtect VMS and they have claims with values that are linked to several roles, the user will get access to the sum of the roles just as if they were added manually to multiple roles.
One thing that isn’t supported, though, is to use the logical “and” and “not” functions to link the external IDP user to the roles only if multiple conditions are true. For example, it is not possible to do the following:
-
Link external IDP users to a role only when a user has two specific claims (“and” function)
-
Reject linking the external IDP users to a role even though they have an appropriate claim, but in addition have a claim that is not allowed (“not” function).
If this kind of functionality is desired, the claims must be configured in the external IDP to provide a single claim with values that represent the result of the desired logical function for the specific external IDP users.
External IDP users in the XProtect VMS
With claims configured both in the external IDP and added to the XProtect VMS roles, the external IDP users will be created automatically in the XProtect VMS when the users are authenticated by the external IDP, and they will have access per the roles they are linked to through their claims.
However, since the external IDP users are linked to the XProtect VMS roles through their claims, the external IDP users are not added to and listed in the specific roles – even if they technically have permissions for the roles per their claims. This is similar to how Microsoft AD users that are members of an AD group are not listed in the role when the AD group is added to a role.
However, unlike the users in AD groups, the external IDP users are auto-provisioned as a kind of basic user in the XProtect VMS upon their login with an XProtect VMS client.
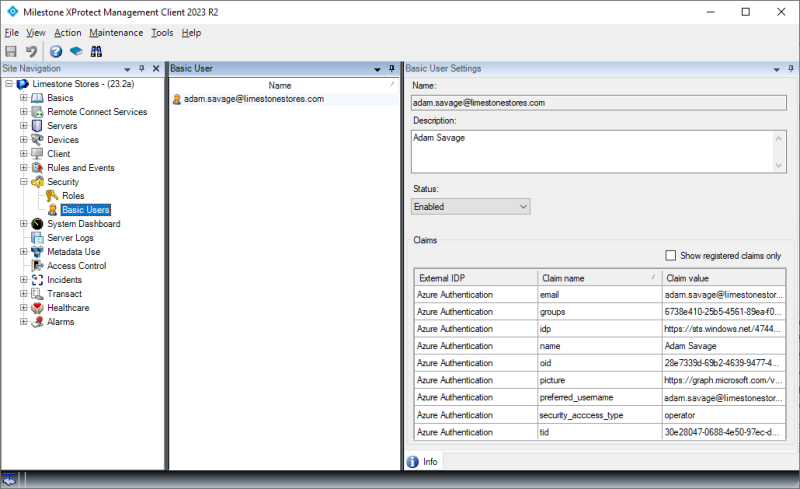 Selecting an external IDP user will provide access to viewing the claims for the user (the ones provided at the latest log in).
Selecting an external IDP user will provide access to viewing the claims for the user (the ones provided at the latest log in).
Furthermore, if required, the external IDP user can be disabled in the XProtect VMS even though the user is still enabled in the external IDP. This is done by changing the ‘Status’ from ‘Enabled’ to ‘Locked out’.
Normally, a user could just be deleted. However, since the users are automatically created when authenticated by the external IDP, this wouldn’t work for external IDP users.
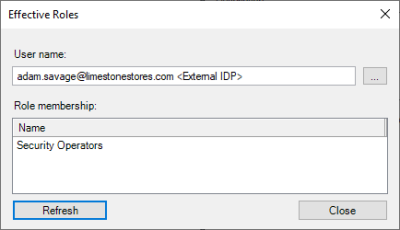
Effective roles
Since external IDP users that get their permissions based on claims are not added and listed in the roles, the information shown in the roles cannot be used to get an overview of which roles the external IDP users are linked to.
This information can, however, be obtained with the effective roles function. The function are available by right-clicking the external IDP user in the basic users list and selecting ‘Effective roles…’
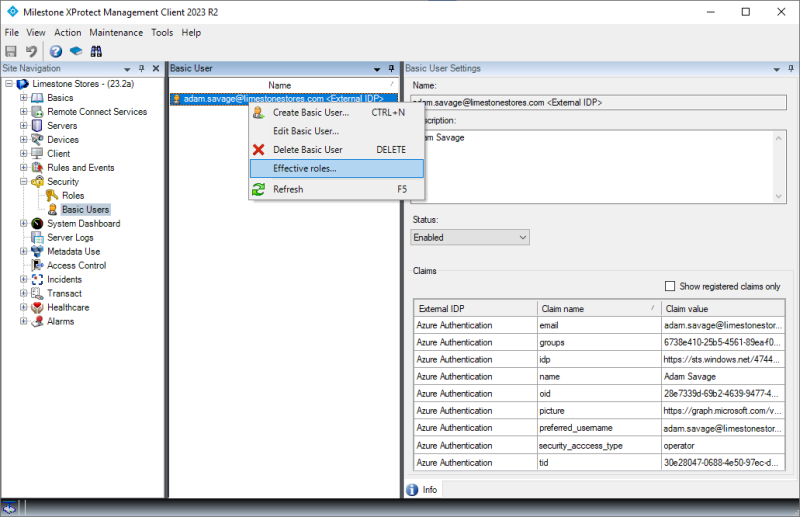
Doing so will open a dialog where the roles that the external IDP user is linked to are listed. The list is based on the claims that the external IDP user had at the latest log in.