Media flow and inherent security risks
In any IP-based video surveillance system, there is an inherent security risk in the different parts, components or communication media used. At each step in the media flow or process there is a risk of unauthorized access, interruption of service, unauthorized interception of media or even media tampering.
In the XProtect VMS, the media flow is typically as illustrated below.
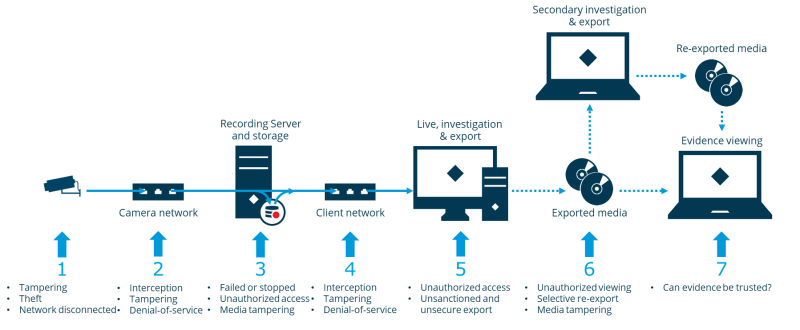
Each step in the media flow has its own inherent risks and threats – of which examples are listed here:
-
Media is captured by a camera
-
Camera may be tampered with by moving it or by covering the lens
-
Camera may be stolen, disconnected, or simply vandalized
-
Media is streamed to the recording server
-
Unauthorized equipment may be connected to the network, potentially enabling the capture and modification of transmitted media streams
-
The network may be disrupted with a denial-of-service attack performed by someone connecting malicious equipment to the network
-
Recording server stores media and provides access for clients
-
Recording server may fail or be turned off
-
Unauthorized access to the recording server could be attempted via the network using either Milestone XProtect Clients or the underlying APIs
-
The recording server and media database files could be compromised by someone obtaining remote or physical access to the recording server and storage system, and thus obtain direct access to the media database files
-
Live or recorded media is sent over the network to the clients
-
Unauthorized equipment may be connected to the network, potentially enabling the capture and modification of transmitted media streams
-
The network may be disrupted with a denial-of-service attack performed by someone connecting malicious equipment to the network
-
Live or recorded media viewed and exported to removable media
-
Unauthorized persons may try to hack or otherwise obtain login credentials to gain access to view and export media
-
Legitimate users of the VMS may export recorded media without proper reason, for instance with the intent to publish “funny” videos on social media such as Facebook or YouTube
-
Exported media is in transit
-
The exported media may be viewed by unauthorized people
-
“Carefully” selected parts of the exported media may be re-exported to make the evidence appear different from the originally exported media, or it may be re-exported to an unsecure format making it possible to post the exported media on social media such as Facebook or YouTubes
-
The exported media may be tampered with by removing, adding, or modifying critical sequences of the recorded media to give another impression of the recorded evidence
-
The exported evidence is viewed
-
The exported media may have been tampered with either in the VMS’s recording server media database or after the media was exported to give another impression of the recorded evidence

