Management Permissions
In addition to the Management Client profiles, XProtect Corporate supports configuring permissions for accessing and managing the VMS, its functions, and the devices in it. In contrast to Management Client profiles which just customizes the user interface, the permissions rigorously control what the administrators actually can access and manage in the VMS. This works in the way that the VMS servers, for every request made, check if the user or the administrator have permissions to access and manage the function or resource in question.
This ensures that users and administrators can only access and manage the different devices and functions in the VMS that they have specifically been granted permissions to, no matter if they use the XProtect Management Client, the MIP SDK or the APIs directly.
Overall Security
The permissions to view and manage the various areas and functions of the VMS are configured by selecting a role (1), and then the ‘Overall Security ’ tab (2). This will show the security groups in the ‘Role Settings’ pane (3). Selecting a security group in the list shows the permissions (4) that can be configured for the selected security group. The permissions available depend on the selected security group.
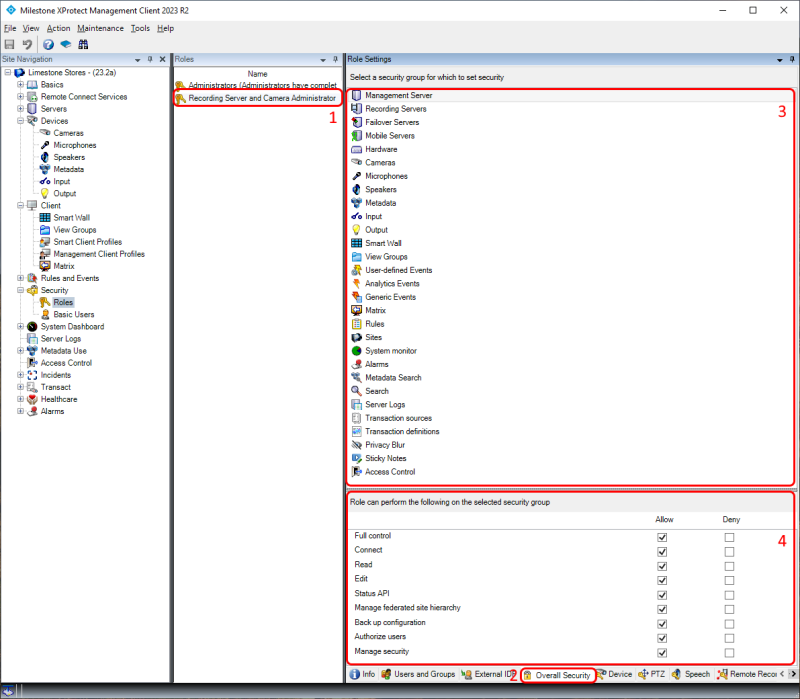
Checking ‘Allow ’ for a function will grant access to the function and checking ‘Deny ’ will deny access. If the user or administrator is a member of two or more roles with conflicting permissions, deny will take precedence.
When configuring permissions to cameras, microphones, speakers, metadata, input and output, the settings apply to all current devices in the system as well as devices that are added later.
Configuration Example
In the example in the previous Management Client profiles section, an administrator role is configured with a profile that provides access to the Management Client elements for managing recording servers and devices (cameras, microphones, speakers, metadata, input and output) only. However, a matching set of permissions must also be configured for the role to ensure that the VMS servers can check the permissions and only allow access to the various resources and functions that the administrator has permissions to.
The permissions needed to enable administrators to just manage recording servers and devices, are configured on the ‘Overall Security ’ tab for a role as shown in the screenshots below.
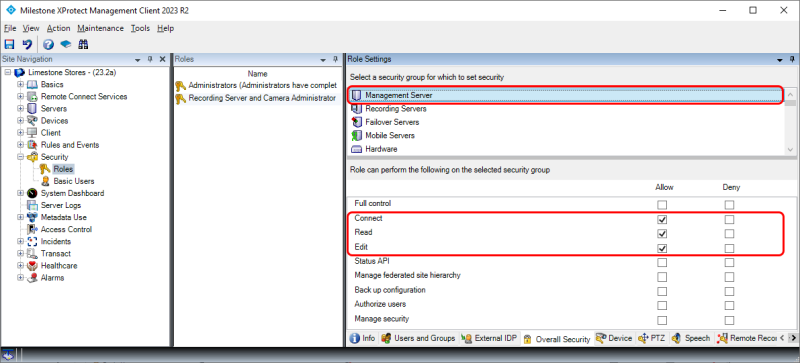
For ‘Management Server’, the following must be allowed as they are required to enable the administrator to log in with the Management Client and edit settings:
-
‘Connect’
-
‘Read’
-
‘Edit’
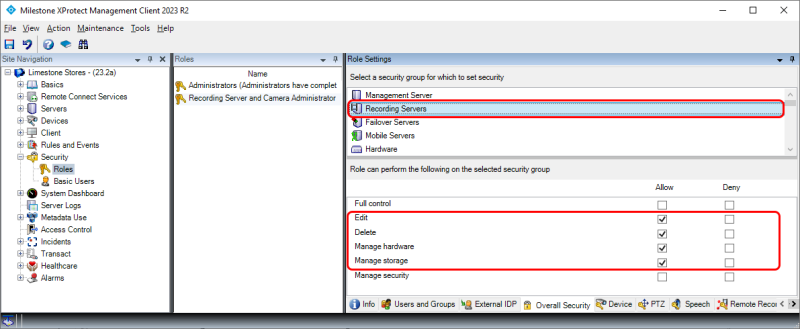
For ‘Recording Server’, the following functions must be allowed:
-
‘Edit’
-
‘Delete’
-
‘Manage Hardware’
-
‘Manage Storage’
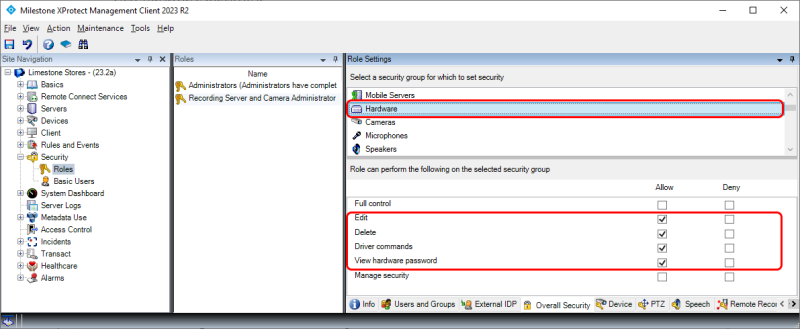
For ‘Hardware’ (devices added to a recording server), the following must be allowed:
-
‘Edit’
-
‘Delete’
-
‘Driver commands’
-
‘View hardware password’
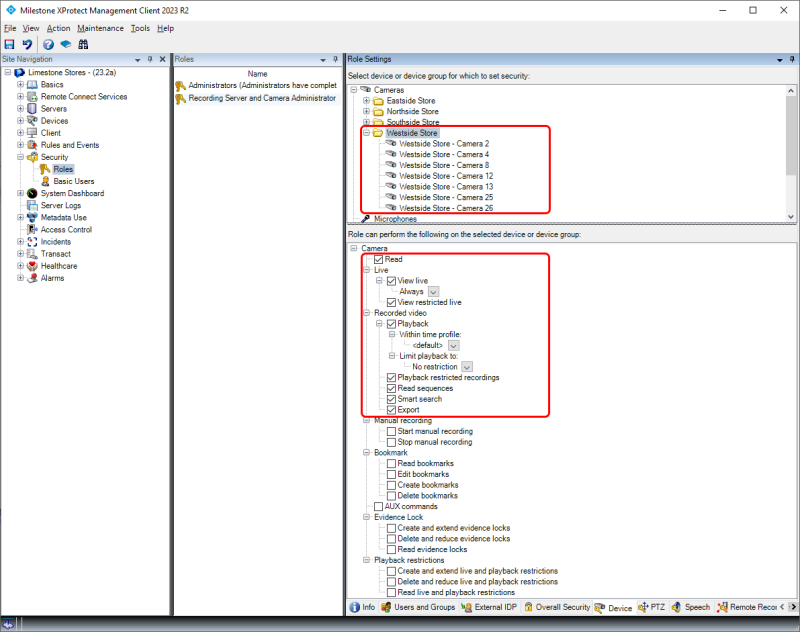
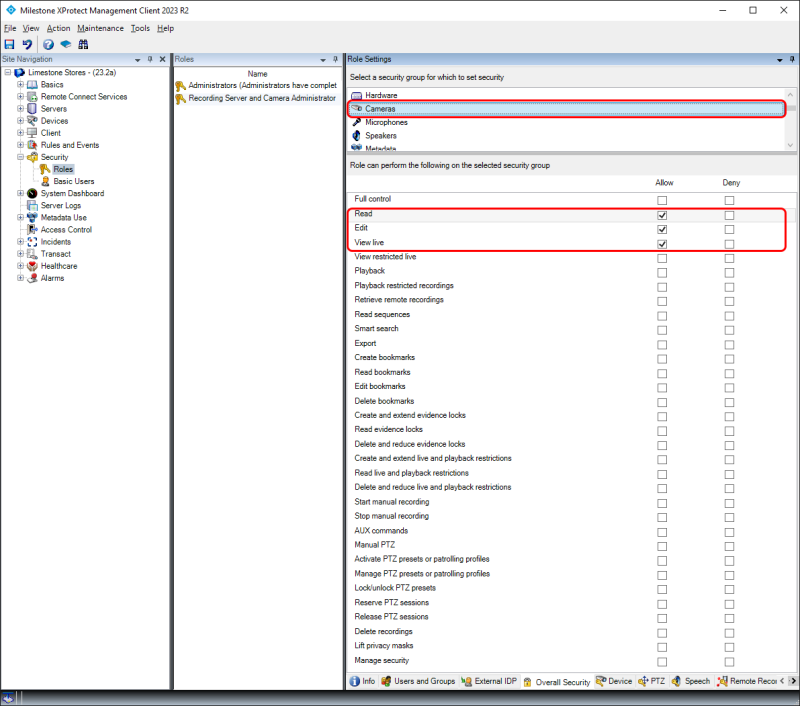
For ‘Cameras’ and the other device types (not shown with screenshots), the following must be allowed:
-
‘Read’
-
‘Edit’
-
‘View live’
With the above permissions settings set, access to managing the VMS functions and the devices will be checked and enforced by the VMS servers. This ensures that administrators in this role can only manage the specific areas of the VMS that they have been granted permissions to - even if using a custom-made 3rd party “Management Tool” that utilizes the MIP SDK or the VMS APIs.
Permission requirements advice
When certain overall permissions are allowed, the XProtect Management Client will notify the administrator that additional permissions are required to obtain access to the feature.
In the example below, the ‘Manage federated site hierarchy’ for the ‘Management Server‘ has been allowed. However, to be able to manage the federated site hierarchy, the administrator must also have access to read federated sites. If permissions to read sites is not given, the administrator technically has permission to manage the federated site hierarchy, but in fact it will not be possible because the information for the federated sites cannot be read.
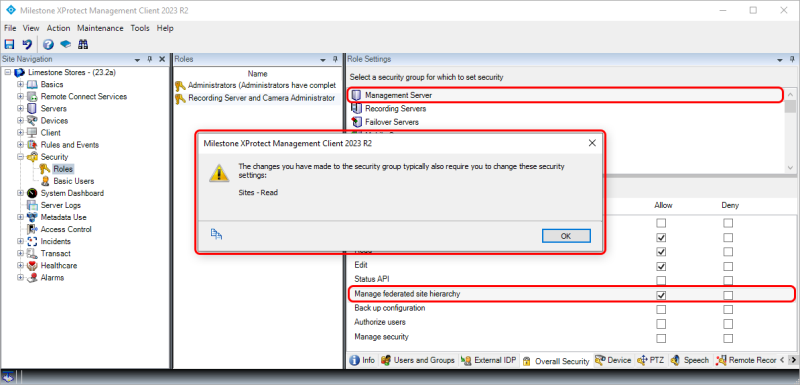
In the example above, the missing permissions are enabled by selecting the ‘Sites’ node and allow ‘Read’ (not shown in a screenshot).
Another case where the XProtect Management Client will notify the administrator that more permissions may be needed is when setting permissions to work with rules.
In this case, the administrator needs additional permissions to configure the rules. This is because rules can be trigged on events from several types of sources and can trigger various VMS actions. If the administrator lacks read permissions to event sources and to the VMS features that are triggered by the events, then it’s technically possible for the administrator to manage rules but not to select triggering events and set actions to perform - making it impossible to properly manage rules.
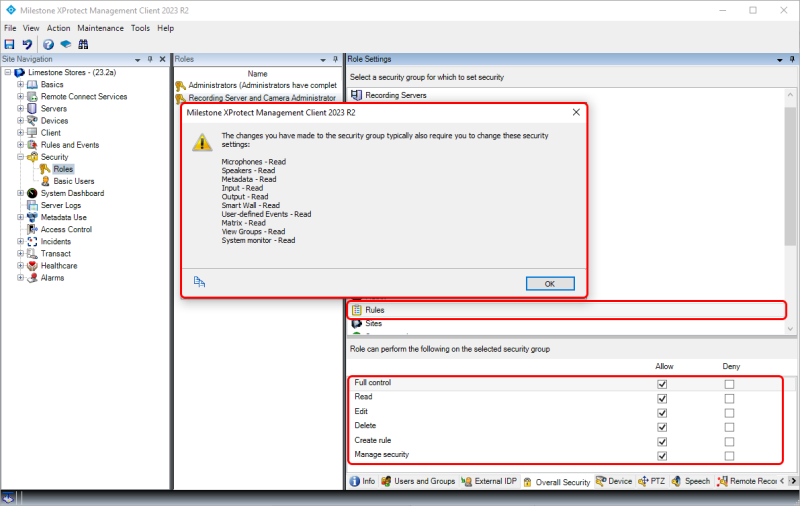
That said, it may be desired to only grant the administrator permissions to a subset of sources and features as it is then possible to limit the sources and actions that the administrator can work with in the rule. For example, the administrator’s permissions could be limited to rules for a specific group of cameras.
If an administrator attempts to work with a rule that includes cameras, that are not covered by the administrator’s read permissions, the sources are listed as: ‘(deleted or restricted device)’.
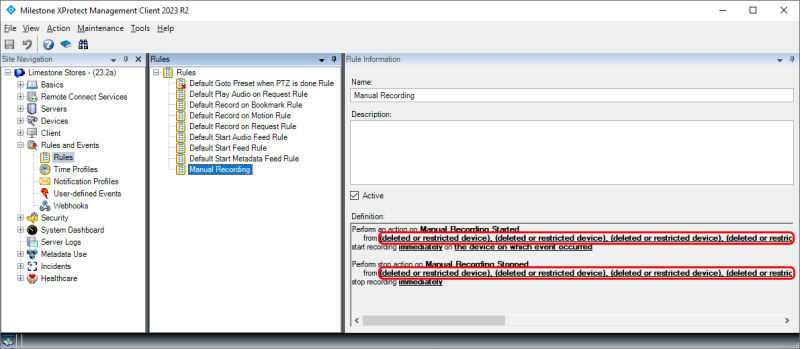
The reason why the rule shows the device name as ‘(deleted or restricted device)’ and not as either “deleted” or “restricted” is that the Management Client’s request to resolve the device ID to its name results in the same answer from the VMS – “device not found”. Therefore, the XProtect Management Client does not know if this is because of missing device permissions or if the device has been deleted.
Missing permission handling
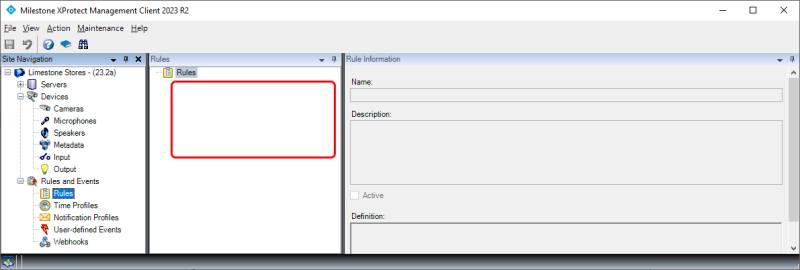
If there is a difference between the Management Client profile and the permissions in the role, the administrator may, in the XProtect Management Client, see empty dialogs, lists or settings as shown in the screenshot below. The administrator in the example has the ability to view rules enabled in the Management Client profile, but does not have security permission to read rules.
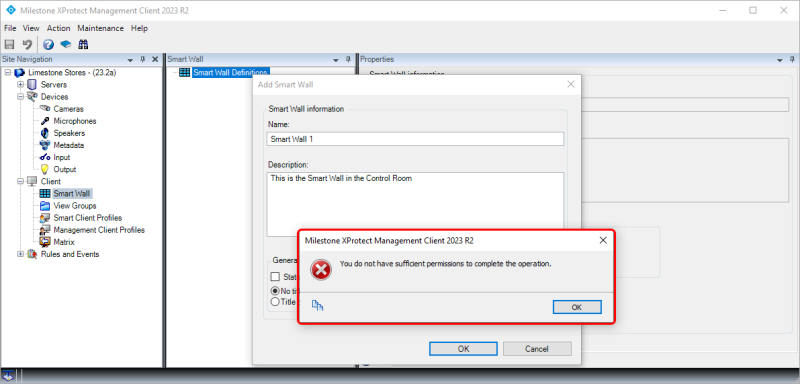
When trying to administrate settings, features or devices, that the administrator does not have
permissions for, the XProtect Management Client will display an error message with information about the
insufficient permissions for this management operation.
Individual device permission
In addition to setting the device permission on the ‘Overall Security’ tab, it is also possible to set permissions for viewing and managing individual devices. This is done on the ‘Device’ tab. Here permissions can be set for a group of devices or for an individual device.