FIPS 140-2 compliance
This section discusses FIPS 140-2 and how to configure and use XProtect VMS to operate in FIPS 140-2 compliant mode.
The terms "FIPS 140-2 compliant" and "FIPS 140-2 compliant mode" are not legally binding. The terms are used here for clarity.
FIPS 140-2 compliant means that software uses FIPS 140-2-validated instances of algorithms and hashing functions in all instances in which encrypted or hashed data is imported to or exported from the software. Additionally, this means that software will manage keys in a secure manner, as is required of FIPS 140-2-validated cryptographic modules. The key management process also includes both key generation and key storage.
FIPS 140-2 compliant mode refers to software that contains both FIPS-approved and non-FIPS approved security methods, where the software has at least one "FIPS mode of operation". This mode of operation only allows for the operation of FIPS-approved security methods. This means that when the software is in the "FIPS mode", a non-FIPS approved method is not used in lieu of the FIPS approved method.
What is FIPS?
Federal Information Processing Standards (FIPS) are a family of standards developed by the following two government bodies:
- The National Institute of Standards and Technology (NIST) in the United States
- The Communications Security Establishment (CSE) in Canada
These standards aim at ensuring computer security and interoperability.
All software solutions deployed in government and highly regulated industries in the United States and Canada are required to comply with FIPS 140-2.
What is FIPS 140-2?
FIPS 140-2, titled "Security Requirements for Cryptographic Modules," specifies which encryption algorithms and which hashing algorithms can be used and how encryption keys are to be generated and managed.
The security requirements specified in this standard are intended to maintain the security provided by a cryptographic module, but conformance to this standard is not sufficient to ensure that a particular module is secure. The operator of a cryptographic module is responsible for ensuring that the security provided by the module is sufficient and acceptable to the owner of the information that is being protected, and that any residual risk is acknowledged and accepted.
Which XProtect VMS applications can operate in a FIPS 140-2 compliant mode?
As of XProtect VMS 2020 R3, all encryption algorithms have been replaced with Microsoft's Cryptography API: Next Generation (CNG), which adheres to the latest security technologies available and is FIPS compliant. That is, all XProtect VMS 2020 R3 applications can operate in FIPS compliant mode.
For the sake of backward compatibility, some non-compliant algorithms and processes persist in XProtect VMS, even after version 2020 R3, but this does not affect the ability to operate the system in FIPS compliant mode.
Is XProtect VMS always FIPS compliant?
No. Some non-compliant algorithms and processes persist in XProtect VMS. But, XProtect VMS can be configured and operate so that it uses only the FIPS 140-2 certified algorithm instances and thereby operate in a FIPS compliant mode.
Should you enable FIPS 140–2 mode?
Before enabling the FIPS 140–2 mode it is necessary to understand whether you need it or not. For instance, if you are working and connected to a US or Canadian government network and infrastructure, then it is mandatory to comply with FIPS 140–2 and enable it on your computer for communication as per the standard. Furthermore, enabling FIPS 140–2 mode on your Windows operating system restricts many programs and services from running, since only FIPS-approved algorithms and services will be supported after that. Therefore, it is advised to check whether there is a necessity or not.
How to ensure XProtect VMS can operate in FIPS 140-2 compliant mode?
In order to operate XProtect VMS in a FIPS 140-2 mode of operation you must:
- Ensure third-party integrations can operate on a FIPS enabled Windows operating system (see Verify third-party integrations)
- Connect to devices in a way that ensures a FIPS 140-2 compliant mode of operation (see Connect devices: background)
- Ensure that data in the media database is encrypted with FIPS 140-2 compliant algorithms (see Media database: Considerations regarding backward compatibility)
- Run Windows operating system in FIPS 140-2 approved mode of operation. See the Microsoft site for information on enabling FIPS.
Considerations regarding upgrade
Upgrading to XProtect VMS 2020 R3 to operate in FIPS compliant mode requires a unique upgrade process. This upgrade process is required only by existing XProtect VMS users who must operate in a FIPS compliant mode.
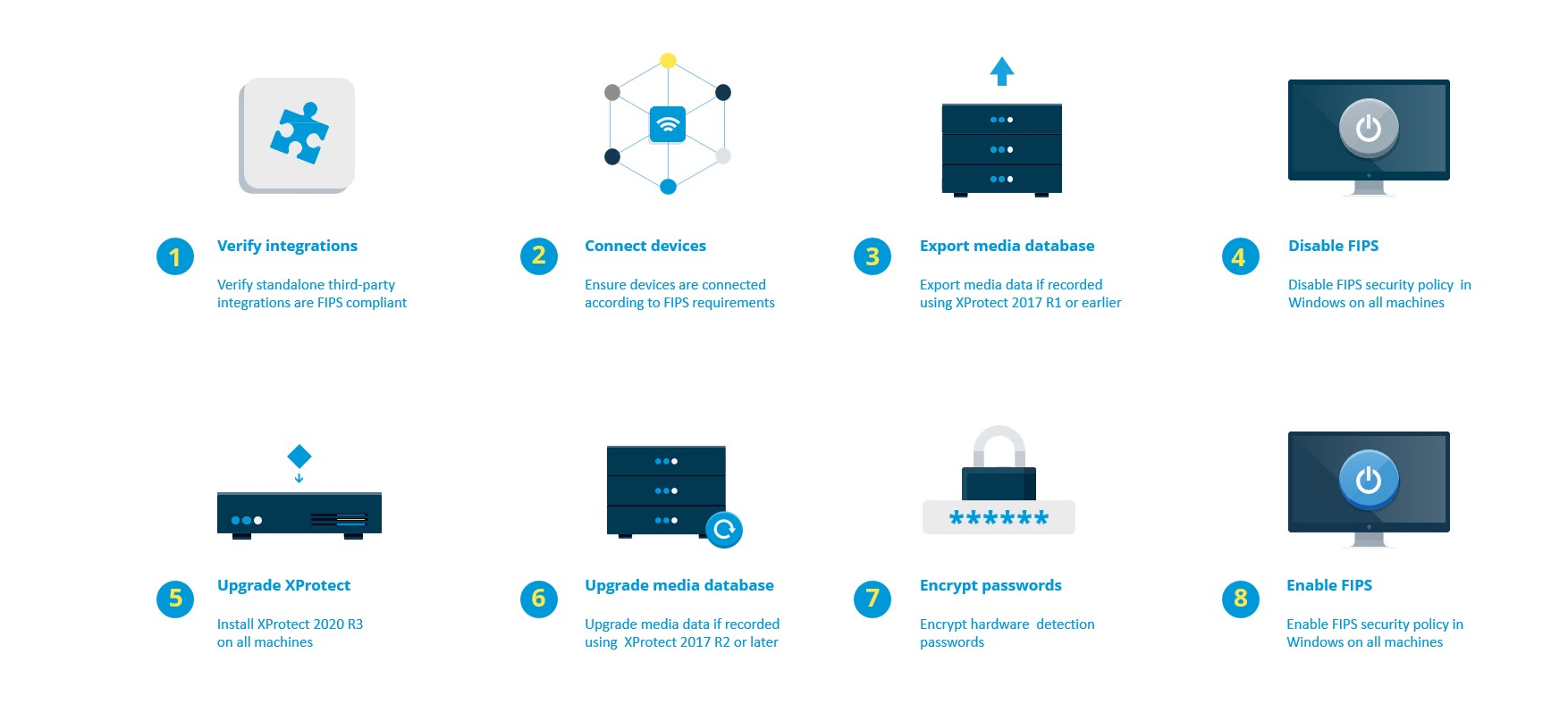
The upgrade process depends on which version of XProtect VMS you are upgrading from.
Recommended upgrade process for customers running XProtect VMS
- Start investigation whether third-party integrations are FIPS 140-2 compliant (see Verify third-party integrations).
- Prepare device connections to be FIPS 140-2 compliant (see Connect devices: background).
- Export recordings made with XProtect VMS versions that are older than 2017 R2 (see Media database: Considerations regarding backward compatibility).
This applies to customers who have encrypted or signed recordings at any point in time.
- Disable FIPS on the Windows operating system (see FIPS Group Policy on the Windows operating system).
- Install XProtect VMS 2025 R2 (see Install XProtect VMS 2025 R2).
- Upgrade the recordings in the media database that are made with XProtect VMS 2019 R3 or earlier (see Media database: Considerations regarding backward compatibility).
- Update the encryption of hardware discovery passwords (see Encrypt hardware detection passwords).
- Enable FIPS on the Windows operating system and restart all of the computers with XProtect VMS installed.
Do not enable FIPS until all of the computers in the XProtect VMS network, including XProtect Smart Client workstations, are prepared for FIPS.
Verify third-party integrations
If an integration is not FIPS 140-2 compliant, it cannot run on a Windows operating system with the FIPS Group Policy flag enabled.
In addition, because of changes made to the MIP SDK in relation to FIPS, integrations that access the feature list in the license must be recompiled.
In order to ensure that the integrations will still work after upgrading to XProtect VMS 2020 R3, you must:
- Make an inventory of all your integrations to XProtect VMS
- Contact the providers of these integrations and ask if the integrations are FIPS 140-2 compliant and whether they foresee that the integrations need to be changed due to the MIP SDK updates
- Deploy the FIPS 140-2 compliant integrations to XProtect VMS after the VMS has been updated
Connect devices: background
If you want to operate XProtect VMS in a FIPS compliant mode, you must make sure that the drivers, and hence the communication to the devices, also adhere to FIPS compliance.
The Milestone XProtect VMS device drivers can be FIPS 140-2 compliant because they can be configured and operate so that they use only FIPS 140-2 compliant algorithm instances. Only specific drivers in a specific configuration are FIPS 140-2 compliant. In this specific FIPS 140-2 configuration the driver will be able to communicate with devices in a compliant way. The devices must fulfill several requirements in order to be able to accept this communication. In addition, the FIPS Group Policy flag must be enabled in Windows on the server where the recording server is installed. When the FIPS Group Policy flag is enabled, the FIPS 140-2 capable drivers will operate in compliant mode and will not use non-approved cryptographic primitives. The drivers will use the algorithms used only for secured channels of communication.
Device connectivity requirements
XProtect VMS is guaranteed and can enforce FIPS 140-2 compliant mode of operation if the following criteria are met:
- Devices use only drivers from the list (Supported drivers) to connect to XProtect VMS
This list shows drivers that can assure and enforce compliance.
- Devices use device pack version 11.1 or higher
Drivers from the legacy driver device packs cannot guarantee a FIPS 140-2 compliant connection.
- Devices are connected over HTTPS and on either Secure Real-Time Transport Protocol (SRTP) or Real Time Streaming Protocol (RTSP) over HTTPS for the video stream
Driver modules cannot guarantee FIPS 140-2 compliance of a connection over HTTP. The connection may be compliant, but there is no guarantee that it is in fact compliant.
- The computer that is running the recording server must have the FIPS Group Policy flag enabled in Windows
Effects of operating in FIPS 140-2 compliant mode
When operating in FIPS 140-2 compliant mode, some drivers will be unavailable for use. Drivers which are listed as FIPS 140-2 might not be able to connect to devices that do not fulfill the device requirements.
A driver is FIPS 140-2 compliant and the communication with the device is FIPS 140-2 compliant if the FIPS 140-2 capable driver:
- Operates in an environment with the FIPS Group Policy enabled
- Is connected to a device that fulfills the device requirements (see Device requirements)
- Is configured properly (see How to configure the device and the driver for FIPS 140-2)
If any of the requirements for FIPS 140-2 compliant mode are not fulfilled, then there is no guarantee about the FIPS 140-2 compliancy of the driver or the communication with the device. See Drivers and FIPS 140-2 for more information.
Devices running over Milestone Open Network Bridge
When running on a computer that has the FIPS Group Policy flag enabled in Windows, the Milestone Open Network Bridge uses SHA-256 as a hashing algorithm. On a computer that does not have FIPS enabled, then you can select either MD5 or SHA-256 for hashing.
Media database: Considerations regarding backward compatibility
It is possible to have recordings in the same storage from several different versions of XProtect VMS at the same time.
Data that is signed or encrypted must be:
- Exported from the storage if it was recorded with XProtect VMSversion 2017 R1 or older
Data export is done by using the XProtect Smart Client.
- Upgraded, if it was recorded with XProtect VMS version 2017 R2 or newer
Data upgrade is done in collaboration with Milestone Support, using a media conversion tool provided by Milestone Support.
The FIPS Group Policy flag must be disabled on the Windows operating system for the media conversion tool to run.
The recording server must also be stopped while the media conversion tool is running, and there are no recordings being made while the tool is running.
Media upgrade depending on XProtect VMS version
- Data recorded with XProtect VMS version 2017 R1 and earlier
Encrypted media data that was recorded with XProtect VMS 2017 R1 and earlier is not available if enabling FIPS, even if the media conversion tool has been run.
Export the media data that was recorded with XProtect VMS 2017 R1 and earlier to access it offline.
See Media database data upgrade: XProtect VMS 2017 R1 and earlier.
- Data recorded with XProtect VMS version 2017 R2 to 2019 R3
Media data that was recorded with XProtect VMS versions 2017 R2 to 2019 R3 will not automatically be re-encrypted. Conversion can be time consuming and should be planned in advance.
To get older data updated to use FIPS compliant algorithms, contact Milestone support to get the media conversion tool.
See Media database upgrade: XProtect VMS 2017 R2 to XProtect VMS 2019 R3.
- Data recorded with XProtect VMS version 2020 R1 or 2020 R2
Media data that was recorded with XProtect VMS 2020 R1 or 2020 R2 will automatically be re-encrypted with FIPS 140-2 compliant algorithms when the recording server is started after an upgrade. See Media database upgrade: XProtect VMS 2020 R1 or XProtect VMS 2020 R2.
Media upgrade details
Re-encrypting the data with a recording server with FIPS compliant algorithms is a central part of the upgrade process. Therefore, the upgrade process varies, based on the version of XProtect VMS used for recording that data.
| Data recorded with | ||||
|---|---|---|---|---|
| 2017 R1 and earlier | 2017 R2 - 2019 R3 | 2020 R1 - 2020 R2 | 2020 R3 and later | |
|
Changes |
Data encrypted with DES Signing using MD5 Passwords:
|
Data encrypted with AES Signing using SHA |
Password list in storage CONFIG.XML Passwords in password list are DES encrypted |
Passwords in password list are encrypted using AES A media conversion tool is available for updating table CONFIG.XML's from having password _a & _b, to use updated password list |
|
FIPS disabled |
All functionality works as expected | |||
| FIPS enabled
Signed data |
Signed data can playback Verify signing during export fails |
Signed data can be played back Verify signing during export works |
||
| FIPS enabled
Encrypted data Media conversion tool not run |
Storage stays offline (Storage may stay offline if encryption was ever enabled for storage) |
All functionality works as expected | ||
| FIPS enabled
No encryption Media conversion tool not run |
All functionality works as expected |
|||
|
Media conversion tool has run |
Media conversion tool may require a lot of time to run because it updates table CONFIG.XML's for all encrypted tables |
Media conversion tool runs fast because it only needs to update storage CONFIG.XML |
Media conversion tool runs fast because no update is needed |
|
| FIPS enabled
Encrypted data Media conversion tool has run |
Encrypted data is not available Connection lost on playback Archiving with Reduce to key-frames archives entire GoP |
Encrypted data can be played back Archiving with Reduce to key-frames works as expected |
||
| FIPS enabled
No encryption No signing Media conversion tool has run |
All functionality works as expected |
|||
Media database data upgrade: XProtect VMS 2017 R1 and earlier
If you are running XProtect VMS version 2017 R1 or earlier or if you have signed or encrypted data recorded with these versions, the recordings are encrypted with algorithms that are not considered secure by the FIPS 140-2 standard.
It is not possible to access these recordings from a computer where the FIPS Group Policy flag is enabled.
As a consequence, it is required to export the media database to a location where it can still be accessed.
Media database upgrade: XProtect VMS 2017 R2 to XProtect VMS 2019 R3
If you are running a version of XProtect VMS between XProtect VMS 2017 R2 and XProtect VMS 2019 R3 and if at any point in time encryption has been enabled in the media database, in order to access these recordings you must do one of the following options.
Both options require the use of the media conversion tool. The recording server must be stopped while the media conversion tool is running, and there are no recordings being made while the tool is running. See What is the media conversion tool? for more information.
- Option 1
Use this option to be able to operate in a FIPS environment immediately, and if you have a long retention time. The time required to run the media conversion tool could be significant.
- Upgrade XProtect VMS to 2020 R3.
- With FIPS disabled on the Windows operating system, run the media conversion tool that is provided by Milestone support.
- Enable the FIPS Group Policy flag on the Windows operating system.
- Option 2
Use this option if operating in a FIPS environment can wait, if you have a short retention time, and if you are running the media conversion tool on less data.
- Upgrade XProtect VMS to 2020 R3.
- Run the XProtect VMS through the retention time without enabling FIPS on the Windows operating system.
- Run the media conversion tool to ensure that all the data is converted to be FIPS compliant.
- Enable the FIPS Group Policy flag on the Windows operating system.
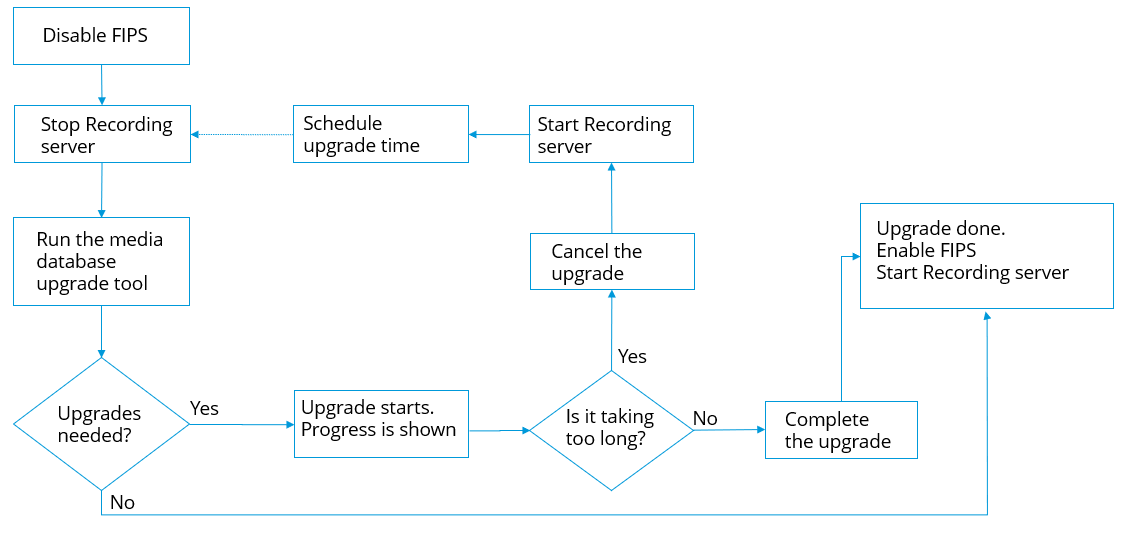
What is the media conversion tool?
The media conversion tool is a stand-alone PowerShell script, that is delivered in source. It is not part of any installation.
It is to be distributed to customers only through Milestone support.
It can convert all storage in bulk, or it can be run on a specific storage.
Progress indicators show how far the tool has gotten.
If the conversion takes too long, you can cancel the job and continue without FIPS enabled.
The media conversion tool converts encrypted credentials inside existing media table files to the newest format that is FIPS compatible.
The media conversion tool does not change the encryption of the video data itself. If the video data is encrypted with a non-compliant algorithm (DES), the updated tables will load, but video will be inaccessible in FIPS compliant mode.
The media conversion tool converts and checks if all tables are using FIPS compliant algorithms.
Approved tables will be marked to eliminate them from being checked by media conversion tool again.
After running the media conversion tool, the XProtect VMS 2020 R3 will be able to load tables in FIPS compliant mode.
Media conversion tool workflow
Media database upgrade: XProtect VMS 2020 R1 or XProtect VMS 2020 R2
If you are running XProtect VMS version 2020 R1 or XProtect VMS 2020 R2, media data that is recorded with one of these versions will be automatically re-encrypted with FIPS 140-2 compliant algorithms during the recording server upgrade.
FIPS Group Policy on the Windows operating system
FIPS mode of operation is enabled and disabled with the FIPS Group Policy flag on the Windows operating system. See the Microsoft site for information on enabling and disabling FIPS.
Before you upgrade, you must disable the FIPS Group Policy flag on all the computers that are part of the XProtect VMS , including the computer that hosts SQL Server and all XProtect Smart Client workstations.
There are two reasons why the FIPS Group Policy flag must be disabled on all computers in the XProtect VMS before you upgrade:
- During the upgrade, data that is encrypted with non-approved FIPS algorithms is re-encrypted with approved algorithms. In order to run the decryption on the Windows operating system, the FIPS Group Policy flag must be disabled.
- If the FIPS Group Policy flag is enabled in Windows, you will not be able to use the XProtect VMS until all components are upgraded. For example, a 2020 R2 XProtect Smart Client will not be able to communicate with a 2020 R3 Management Server if the Management Server is on a computer that has the FIPS Group Policy flag enabled.
FIPS Group Policy and Milestone Federated Architecture
If any site in a Milestone Federated Architecture must operate with the FIPS Group Policy flag enabled in Windows, then all of the sites must also operate with the FIPS Group Policy flag enabled in Windows.
In consequence, the entire Milestone Federated Architecture installation must be upgraded to version 2020 R3.
Install XProtect VMS 2025 R2
When you upgrade, the XProtect VMS installer will check the FIPS security policy and will prevent the upgrade from starting if FIPS is enabled.
Encrypt hardware detection passwords
The hardware detection passwords must be updated after you upgrade to XProtect VMS 2020 R3.
The encryption of the hardware detection passwords is not updated during upgrade from earlier version of XProtect VMS . But, these passwords cannot be read if the FIPS Group Policy flag is enabled in Windows.
You must trigger a conversion of these passwords before you enable FIPS. Do the following:
- Make sure the FIPS Group Policy flag is disabled in Windows.
- In XProtect Management Client, open the Add Hardware wizard.
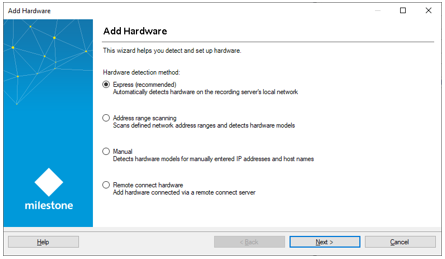
- Select the detection method to open the hardware detection page.
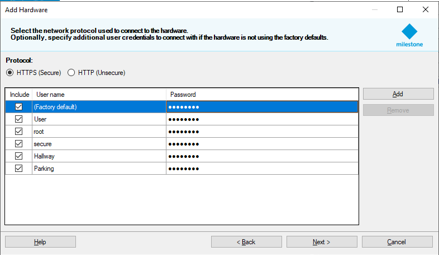
This triggers the re-encryption of the hardware detection passwords with FIPS-compliant algorithms.
The credentials are now encrypted with FIPS-compliant algorithms.

