Advanced steps – Servers, Workstations, Clients and Applications
Adopt standards for secure network and VMS implementations
Milestone recommends that you adopt standards for secure networking and XProtect VMS implementations. The use of standards is a basic component of Internet and network engineering, and the basis of interoperability and system conformance. This also applies to the use of cryptographic solutions, where standards-based cryptography is the most commonly accepted approach.
Establish an incident response plan
Milestone recommends you start with a set of policies and procedures and establish an incident response plan. Designate staff to monitor the status of the system and respond to suspicious events. For example, activities that happen at unusual times. Establish a security Point of Contact (POC) with each of your vendors, including Milestone.
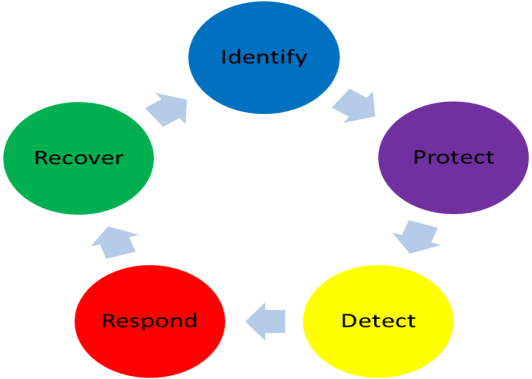
The following image is adapted from the NIST Cybersecurity Framework (https://www.nist.gov/cyberframework). It shows the lifecycle that needs to be considered when creating a plan. The supporting material in the framework provide details about the lifecycle and security controls for incident response plans.
Learn more
The following control(s) provide additional guidance:
- NIST SP 800-53 IR 1-13 Incident Response
Protect sensitive VMS components
Milestone recommends that you use physical access control, and use the VMS to monitor and protect its sensitive VMS components. Physical restriction and role-based physical access control are countermeasures that keep servers and workstations secure.
Administrators and users should only have access to the information they need in order to fulfill their responsibilities. If all internal users have the same access level to critical data, it’s easier for attackers to access the network.
Learn more
The following control(s) provide additional guidance:
- NIST SP 800-53 PE-1 Physical and Environmental Protection Policy and Procedures
- NIST SP 800-53 PE-2 Physical Access Authorizations
- NIST SP 800-53 PE-3 Physical Access Control
- NIST SP 800-53 AC-4 Least Privilege
Follow Microsoft OS Security best practices
Milestone recommends that you follow the security best practices for Microsoft operating systems (OS) to mitigate OS risks and maintain security. This will help you keep the Microsoft servers and client computers secure.
For more information, see Microsoft Security Update Guide (https://msrc.microsoft.com/update-guide).
Use tools to automate or implement the security policy
Milestone recommends that you find one or more tools to help you automate and implement the security policy. Automation reduces the risk of human error and makes it easier to manage the policy. For example, you can automate the installation of security patches and updates on servers and client computers.
One way to implement this recommendation is to combine the Microsoft Security Configuration Manager (SCCM) with the Security Content Automation Protocol (SCAP).(See for example, Geek of All Trades: Automate Baseline Security Settings (https://technet.microsoft.com/en-us/magazine/ff721825.aspx) and Security Content Automation Protocol (SCAP) Validation Program (https://csrc.nist.gov/projects/scap-validation-program).) This gives you a framework to create, distribute, and validate security settings on computers across your network.
Learn more
The following control(s) provide additional guidance:
- NIST SP 800-53 CM-1 Configuration Management Policy and Procedures
- NIST SP 800-53 CM-2 Baseline Configuration
- NIST SP 800-53 CM-3 Configuration Change Control
Follow established network security best practices
Milestone recommends that you follow IT and vendor best practices to ensure that devices on your network are securely configured. Ask your vendors to provide this information. It is important to open and maintain a security dialogue, and a discussion of best practices is a good place to start.
It is important to deny access to the VMS by not using vulnerable network settings. For more information, see SP 800-128 (https://csrc.nist.gov/publications/detail/sp/800-128/final), SP 800-41-rev1 (https://csrc.nist.gov/publications/detail/sp/800-41/rev-1/final) (specific to firewalls), and CISA’s role in industrial control systems (https://www.cisa.gov/ics) (general list).
Learn more
The following control(s) provide additional guidance:
- NIST 800-53 CM-6 Configuration Settings
- NIST 800-53 MA-3 Maintenance Tools

