Introduction to certificates
安全超文本传输协议 (HTTPS) 是超文本传输协议 (HTTP) 的扩展,用于通过计算机网络进行安全通信。 在 HTTPS 中,通信协议使用传输层安全 (TLS) 或其前身安全套接字层 (SSL) 进行加密。
在 XProtect VMS 中,安全通信是通过使用 TLS/SSL 和非对称加密 (RSA) 实现。
TLS/SSL 使用一对密钥(一个私钥和一个公钥)来验证、保护和管理安全连接。
证书颁发机构 (CA) 是任何能够颁发根证书的人。这可以是颁发根证书的互联网服务,或任何手动生成并发放证书的人。CA 可以向 web 服务,即向任何使用 https 通信的软件颁发证书。此证书包含两个密钥,即私钥和公钥。公钥通过安装公共证书安装在 Web 服务的客户端(服务客户端)上。 私钥用于签署必须安装在服务器上的服务器证书。 每当服务客户端调用 Web 服务时,Web 服务都会将包含公钥的服务器证书发送到客户端。服务客户端可以使用已安装的公共 CA 证书验证服务器证书。 客户端和服务器现在可以使用公共和私人服务器证书来交换密钥,从而建立安全的 TLS/SSL 连接。
对于手动发放的证书,必须在客户端可以进行此类验证前安装证书。
有关 TLS 的更多信息,请参阅传输层安全。
In XProtect VMS, the following locations are where you can enable TLS/SSL encryption:
- In the communication between the management server and the recording servers, event servers, and mobile servers
- On the recording server in the communication with clients, servers, and integrations that retrieve data streams from the recording server
- In the communication between clients and the mobile server
In this guide, the following are referred to as clients:
- XProtect Smart Client
- Management Client
- Management Server (for System Monitor and for images and AVI video clips in email notifications)
- XProtect Mobile Server
- XProtect Event Server
- XProtect LPR
- Milestone Open Network Bridge
- XProtect DLNA Server
- Sites that retrieve data streams from the recording server through Milestone Interconnect
- Third-party MIP SDK integrations that support HTTPS
- If the integrations are made using MIP SDK libraries, they need to be rebuilt with MIP SDK 2019 R1
- If the integrations communicate directly with the Recording Server APIs without using MIP SDK libraries, the integrators must add HTTPS support themselves
- If in doubt, ask your vendor who supplied the integration
Certificate distribution
The graphic illustrates the basic concept of how certificates are signed, trusted, and distributed in XProtect VMS.
 A certificate authority (CA) is anyone who can issue root certificates. A CA certificate acts as a trusted third-party, trusted by both the subject/owner (server) and by the party that verifies the certificate (clients) ( see Create CA certificate).
A certificate authority (CA) is anyone who can issue root certificates. A CA certificate acts as a trusted third-party, trusted by both the subject/owner (server) and by the party that verifies the certificate (clients) ( see Create CA certificate).
 The public certificate must be trusted on all client computers. In this way the clients can verify the validity of the certificates issued by the CA (see Install certificates on the clients).
The public certificate must be trusted on all client computers. In this way the clients can verify the validity of the certificates issued by the CA (see Install certificates on the clients).
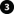 The CA certificate is used to issue private server authentication certificates to the servers (see Create SSL certificate).
The CA certificate is used to issue private server authentication certificates to the servers (see Create SSL certificate).
 The created private SSL certificates must be imported to the Windows Certificate Store on all servers (see Import SSL certificate).
The created private SSL certificates must be imported to the Windows Certificate Store on all servers (see Import SSL certificate).
Requirements for the private SSL certificate:
- Issued to the server so that the server's host name is included in the certificate, either as subject (owner) or in the list of DNS names that the certificate is issued to
- Trusted on all computers running services or applications that communicate with the service on the servers, by trusting the CA certificate that was used to issue the SSL certificate
- The service account that runs the server must have access to the private key of the certificate on the server.
Certificates have an expiry date. You will not receive a warning when a certificate is about to expire. If a certificate expires, the clients will no longer trust the server with the expired certificate and thus cannot communicate with it.
To renew the certificates, follow the steps in this guide as you did when you created certificates.