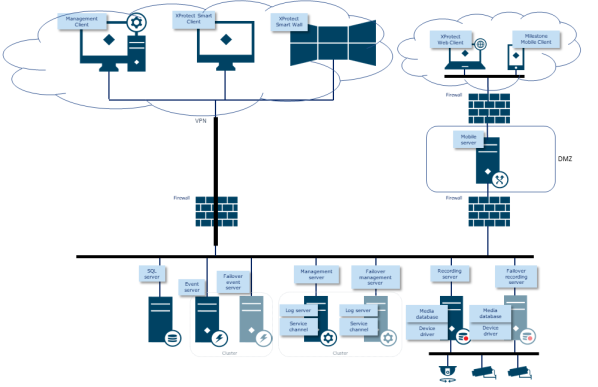
Overview
To help secure your surveillance system, Milestone recommends the following:
- Restrict access to servers. Keep servers in locked rooms, and make it difficult for intruders to access network and power cables.
(PE2 and PE3 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (PE Physical and Environment Protection).)
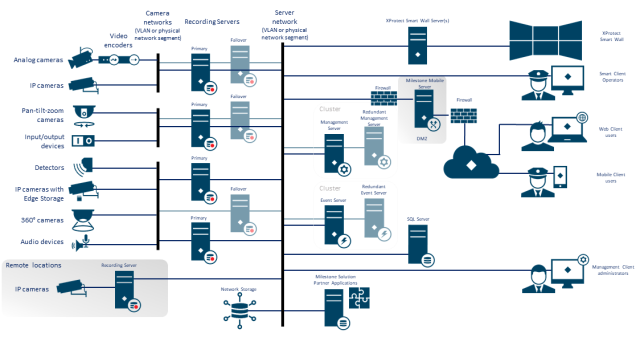
- Design a network infrastructure that uses physical network or VLAN segmentation as much as possible.
(SC3 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (SC System and Communication Protection).)
- Separate the camera network from the server network by having two network interfaces in each recording server: one for the camera network, and one for the server network.
- Put the mobile server in a "demilitarized zone" (DMZ) with one network interface for public access, and one for private communication to other servers.
(SC7 in Appendices D and F NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf).)
- Many precautions can be taken when it comes to general set up. In addition to firewalls, these include techniques to segment the network and control access to the servers, clients and applications.
(AC3, AC4, AC6, CA3, CM3, CM6, CM7, IR4, SA9, SC7, SC28, SI3, SI 8 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (AC Access Controls), (CM Configuration Management) (IR Incident Response) (SA System and Service Acquisition) (SI Systems and Information Integrity).)
- Configure the VMS with roles that control access to the system, and designate tasks and responsibilities.
(AC2, AC3, AC6, AC16, AC25, AU6, AU9, CM5, CM11, IA5, PL8, PS5, PS7, SC2, SI7, in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (AU Audit and Accountability) (IA Identification and Authentication) (PL Planning).)
The figure shows an example of a general setup.
Privacy by design
Milestone products are designed to deliver secure, end-to-end communication. Milestone products are designed to protect privacy and to secure data. Data protection is always important, but especially if you intend to be General Data Protection Regulation (GDPR) compliant in the EU.
According to GDPR, the controller of personal data, when processing such data, has an obligation to implement technical or organizational measures which are designed to implement the data protection principles set out in GDPR. GDPR refers to this as privacy by design.
In the context of a surveillance camera, a relevant example of privacy by design would be a feature that digitally allows the user to restrict image capture to a certain perimeter, preventing the camera from capturing any imagery outside this perimeter that would otherwise be captured.
In XProtect, there is support for privacy masking in two forms – permanent masks that cannot be removed, and liftable masks that (with the appropriate permissions) can be lifted to reveal the image behind the mask.
The controller also has an obligation to implement technical or organizational measures which by default ensure the least privacy intrusive processing of the personal data in question. GDPR refers to this as privacy by default. In the context of a camera, a relevant example of privacy by default could be using privacy masking to keep a sensitive area within the view of the camera private.
What should you do to ensure privacy by design?
- Consider the resolution of different points in the camera scene and document these settings
Different purposes require different image qualities. When identification is not necessary, the camera resolution and other modifiable factors should be chosen to ensure that no recognizable facial images are captured.
- Encrypt your recordings
Milestone recommends that you secure your recordings by enabling at least Light encryption on your recording servers' storage and archives. Milestone uses the AES-256 algorithm for encryption. When you select Light encryption, only a part of the recording is encrypted. When you select Strong encryption, the entire recording is encrypted.
- Secure the network
Milestone recommends that you select cameras that support HTTPS. It is recommended that you set the cameras on separate VLANs and use HTTPS for your camera to recording server communication.
It is recommended that XProtect Smart Clients and XProtect Smart Walls are on the same VLAN as the servers.
Use a VPN encrypted network or similar if using Smart Client or Smart Wall from a remote location.
- Enable and document the intended retention time
According to Article 4(1)(e) of the GDPR, recordings must not be retained longer than necessary for the specific purposes for which they were made. Milestone recommends that you set the retention time according to regional laws and requirements, and in any case, to set the retention time to a maximum of 30 days.
- Secure exports
Milestone recommends that you only allow access to export functionality for a select set of users that need this permission.
Milestone also recommends that the Smart Client profile is changed to only allow export in XProtect Format with encryption enabled. AVI and JPEG exports should not be allowed, because they can not be made secure. This makes export of any evidence material password protected, encrypted and digitally signed, making sure forensic material is genuine, untampered with and viewed by the authorized receiver only.
- Enable privacy masking – permanent or liftable
Use privacy masking to help eliminate surveillance of areas irrelevant to your surveillance target.
Milestone recommends that you set a liftable blurring mask for sensitive areas and in places where person identification is not allowed. Create then a second role that can authorize the mask to be lifted.
- Restrict access permissions with roles
Apply the principle of least privilege (PoLP).
Milestone recommends that you only allow access to functionality for a select set of users that need this permission. By default, only the system administrator can access the system and perform tasks. All new roles and users that are created have no access to any functions until they are deliberately configured by an administrator.
Set up permissions for all functionality, including: viewing live video and recordings, listening to audio, accessing metadata, controlling PTZ cameras, accessing and configuring Smart Wall, lifting privacy masks, working with exports, saving snapshots, and so on.
Grant access to only the cameras that the specific operator needs to access, and restrict access to recorded video, audio, and metadata for operators, either completely, or grant access to only the video, audio, or metadata recorded in the past few hours or less.
Regularly assess and review roles and responsibilities for operators, investigators, system administrators and others with access to the system. Does the principle of least privilege still apply?
- Enable and use two-step verification
Milestone recommends that you specify an additional login step for users of XProtect Mobile or XProtect Web Client by enabling two-step verification.
- Restrict administrator permissions
Milestone recommends that you limit the number of users that have an Administrator role. If you need to create multiple Administrator roles, you can restrict their access by creating Administrator roles that can manage only select parts of the system, such as certain devices or functions.
Milestone also recommends that the VMS administrator does not have full administrator permissions on the storage that contains recorded video, and the storage administrator should not have access to the VMS or backup administration.
For security, segment the network so there is a client/management network, and camera networks behind the recording servers:
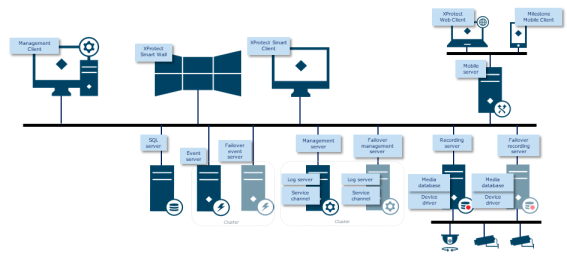
For greater security, put the mobile server in a "demilitarized zone" (DMZ) with one network interface for public access, and one for private communication to other servers, and use VPN encrypted networks for external connections or to increase security for less secure internal networks: