Introduction to certificates
Hypertext Transfer Protocol Secure (HTTPS) ist eine Erweiterung des Hypertext Transfer Protocol (HTTP) für die sichere Kommunikation über ein Computernetzwerk. In HTTPS wird das Kommunikationsprotokoll mithilfe der Transport Layer Security (TLS) oder ihrem Vorläufer, Secure Sockets Layer (SSL), verschlüsselt.
In XProtect VMS wird die sichere Kommunikation dadurch hergestellt, dass SSL/TLS mit asymmetrischer Verschlüsselung (RSA) verwendet wird.
Das SSL/TLS-Protokoll verwendet zwei Schlüssel—einer privat, einer öfftenlich—zur Authentifizierung, Sicherung und Verwaltung sicherer Verbindungen.
Eine Zertifizierungsstelle (Certificate Authority (CA)) kann Web-Diensten auf Servern mithilfe eines CA-Zertifikates Zertifikate ausstellen. Dieses Zertifikat enthält zwei Schlüssel, einen privaten und einen öffentlichen. Der öffentliche Schlüssel wird auf den Clients eines Web-Dienstes (Dienst-Clients) installiert, indem ein öffentliches Zertifikat installiert wird. Der private Schlüssel dient dazu, Serverzertifikate zu signieren, die auf dem Server installiert werden müssen. Jedes Mal, wenn ein Dienst-Client den Web Service anruft, sendet der Web Service dem Client das Server-Zertifikat, einschließlich des öffentlichen Schlüssels. Der Dienst-Client kann das Serverzertifikat mithilfe des bereits installierten, öffentlichen CA-Zertifikates überprüfen. Client und Server können jetzt mit den öffentlichen und privaten Serverzertifikaten einen geheimen Schlüssel austauschen und somit eine sichere SSL/TLS-Verbindung herstellen.
Weitere Informationen zu TLS finden Sie unter https://en.wikipedia.org/wiki/Transport_Layer_Security
In XProtect VMS, the following locations are where you can enable SSL/TLS encryption:
- In the communication between the management server and the recording servers
- On the recording server in the communication with clients, servers and integrations that retrieve data streams from the recording server
- In the communication from clients to the mobile server
In this guide, the following are referred to as clients:
- XProtect Smart Client
- Management Client
- Management Server (for System Monitor and for images and AVI video clips in email notifications)
- XProtect Mobile Server
- XProtect Event Server
- XProtect LPR
- Milestone Open Network Bridge
- XProtect DLNA Server
- Sites that retrieve data streams from the recording server through Milestone Interconnect
- Some third-party MIP SDK integrations
Certificate distribution
The graphic illustrates the basic concept of how certificates are signed, trusted, and distributed in XProtect VMS.
 A CA certificate acts as a trusted third-party, trusted by both the Subject/owner (server) and by the party that verifies the certificate (clients) ( see Create CA certificate).
A CA certificate acts as a trusted third-party, trusted by both the Subject/owner (server) and by the party that verifies the certificate (clients) ( see Create CA certificate).
 The public CA certificate must be trusted on all client computers. In this way the clients can verify the validity of the certificates issued by the CA (see Install certificates on the clients).
The public CA certificate must be trusted on all client computers. In this way the clients can verify the validity of the certificates issued by the CA (see Install certificates on the clients).
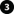 The CA certificate is used to issue private server authentication certificates to the servers (see Create SSL certificate).
The CA certificate is used to issue private server authentication certificates to the servers (see Create SSL certificate).
 The created private SSL certificates must be imported to the Windows Certificate Store on all servers (see Import SSL certificate).
The created private SSL certificates must be imported to the Windows Certificate Store on all servers (see Import SSL certificate).
Requirements for the private SSL certificate:
- Issued to the server so that the server's host name is included in the certificate, either as subject (owner) or in the list of DNS names that the certificate is issued to
- Trusted on all computers running services or applications that communicate with the service on the servers, by trusting the CA certificate that was used to issue the SSL certificate
- The service account that runs the server must have access to the private key of the certificate on the server.
Certificates have an expiry date. XProtect VMS will not warn you when a certificate is about to expire. If a certificate expires, the clients will no longer trust the server with the expired certificate and thus cannot communicate with it.
To renew the certificates, follow the steps in this guide as you did when you created certificates.