Use Windows users with Active Directory
There are two types of users in XProtect VMS:
- Basic user: a dedicated VMS user account authenticated by a combination of username and password using a password policy. Basic users connect to the VMS using a secure socket layer (SSL) with current Transport Layer (TLS) security protocol session (https://datatracker.ietf.org/wg/tls/charter/) for login, encrypting the traffic contents and username and password.
- Windows user: the user account is specific to a machine or a domain, and it is authenticated based on the Windows login. Windows users connecting to the VMS can use Microsoft Windows Challenge/Response (NTML) for login, Kerberos (see Kerberos authentication (explained)), or other SSP options from Microsoft (https://msdn.microsoft.com/en-us/library/windows/desktop/aa380502(v=vs.85).aspx).
Milestone recommends that, whenever possible, you use Windows users in combination with Active Directory (AD) to authorize access to the VMS. This allows you to enforce:
- A password policy that requires users to change their password regularly
- Brute force protection, so that the Windows AD account is blocked after a number of failed authentication attempts, again in line with the organization password policy
- Multi-factor authentication in the VMS, particularly for administrators
- Role-based permissions, so you can apply access controls across your domain
If your organization does not use AD, you can add Windows users to workgroups on the management server instead. Workgroups give you some of the same advantages as Windows users with AD. You can enforce a password policy, which helps protect against brute force attacks, but Milestone recommends that you use a Windows Domain because this gives you central control over user accounts.
Windows users have the advantage of being authenticated via the directory as a single authoritative source and enterprise service for the network and not ad hoc for their local machine. This lets you use role based access controls to assign permissions to users and groups consistently across the domain and the computers on the network.
If you use local Windows users, the user must create a local user name and password on each machine, which is problematic from security and usability perspectives.
To add Windows users or groups to roles in Management Client, follow these steps:
- Open Management Client.
- Expand the Security node.
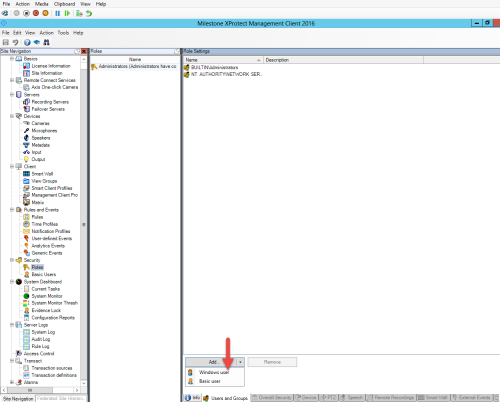
- Select the role to which you want to add the Windows users.
- On the Users and Groups tab, click Add, and select Windows user. A pop-up window appears.
- If the domain name does not appear in the From this location field, click Locations.
- Specify the Windows user, and then click OK.
To verify that the Windows user is an AD user, the domain name must appear as a prefix, for example "Domain\John".
Learn more
The following control(s) provide additional guidance:
- NIST SP 800-53 CM-6 Configuration Settings
- NIST SP 800-53 SA-5 Information System Documentation
- NIST SP 800-53 SA-13 Trustworthiness
Was this article helpful?
Thanks for your feedback!

