General setup
To help secure your surveillance system, Milestone recommends the following:
- Restrict access to servers. Keep servers in locked rooms, and make it difficult for intruders to access network and power cables.
(PE2 and PE3 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (PE Physical and Environment Protection).)
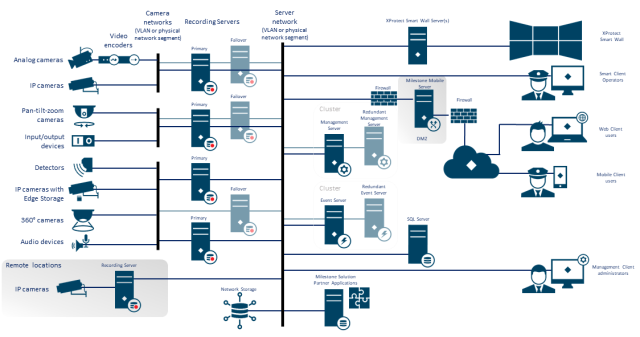
- Design a network infrastructure that uses physical network or VLAN segmentation as much as possible.
(SC3 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (SC System and Communication Protection).)
- Separate the camera network from the server network by having two network interfaces in each recording server: one for the camera network, and one for the server network.
- Put the mobile server in a "demilitarized zone" (DMZ) with one network interface for public access, and one for private communication to other servers.
(SC7 in Appendices D and F NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf).)
- Many precautions can be taken when it comes to general set up. In addition to firewalls, these include techniques to segment the network and control access to the servers, clients and applications.
(AC3, AC4, AC6, CA3, CM3, CM6, CM7, IR4, SA9, SC7, SC28, SI3, SI 8 in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (AC Access Controls), (CM Configuration Management) (IR Incident Response) (SA System and Service Acquisition) (SI Systems and Information Integrity).)
- Configure the VMS with roles that control access to the system, and designate tasks and responsibilities.
(AC2, AC3, AC6, AC16, AC25, AU6, AU9, CM5, CM11, IA5, PL8, PS5, PS7, SC2, SI7, in Appendices D and F in NIST SP 800-53 Rev4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) (AU Audit and Accountability) (IA Identification and Authentication) (PL Planning).)
The figure shows an example of a general setup.
Was this article helpful?
Thanks for your feedback!

