Cyber Risk Management Framework
The security and privacy controls in SP 800-53 Revision 4 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf) are part of an overall risk management framework from NIST. The NIST document SP800-39 (http://csrc.nist.gov/publications/nistpubs/800-39/sp800-39-final.pdf) is a guide to applying a risk management framework. SP800-36 is a foundational document for the NIST Cybersecurity Framework, which is described in Cybersecurity Framework (http://www.nist.gov/cyberframework/).
The figures here show:
- An overview of the risk management process. It shows a high-level, overall approach.
- Risk management at a business level, taking strategic and tactical considerations into account.
- The lifecycle of a risk management framework, and the NIST documents that provides details for each of the steps in the lifecycle.
Security and privacy controls represent specific actions and recommendations to implement as part of a risk management process. It’s important that the process includes the assessment of the organization, the particular requirements of a given deployment, and the aggregation of these activities into a security plan. SP 800-18 Revision 1 (http://csrc.nist.gov/publications/nistpubs/800-18-Rev1/sp800-18-Rev1-final.pdf) provides references for detailed security plans.
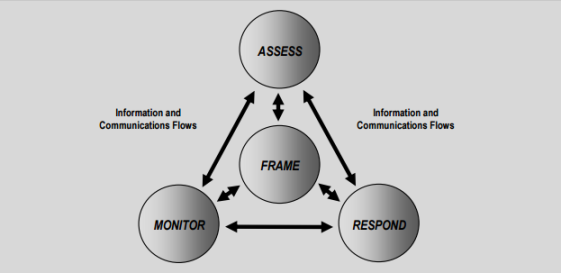
High-level view of risk management (SP 800-39, page 8 (http://csrc.nist.gov/publications/nistpubs/800-39/sp800-39-final.pdf))
The process is interactive, and responses and their outcomes are iterative. Security threats, risks, responses and results are dynamic and adapt, and as a result so must a security plan.
This diagram shows how a risk management framework considers IT systems, business processes, and the organization as a whole to find a balance for the security plan.
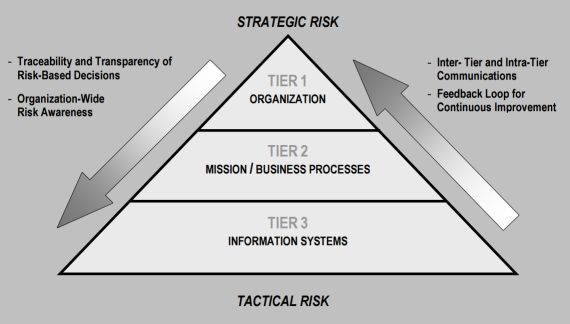
Balancing security and business goals (SP 800-39, page 9 (http://csrc.nist.gov/publications/nistpubs/800-39/sp800-39-final.pdf))
When hardening a system, you balance the impact on business productivity and usability for the sake of security, and vice versa, in the context of the services you deliver. Security guidance is not isolated from other business and IT activities.
For example, when a user enters their password incorrectly on three consecutive attempts, the password is blocked and they cannot access the system. The system is secure from brute-force attacks, but the unlucky user cannot use the device to do their work. A strong password policy that requires 30 character passwords, and changing passwords every 30 days is a best practice, but it’s also difficult to use.
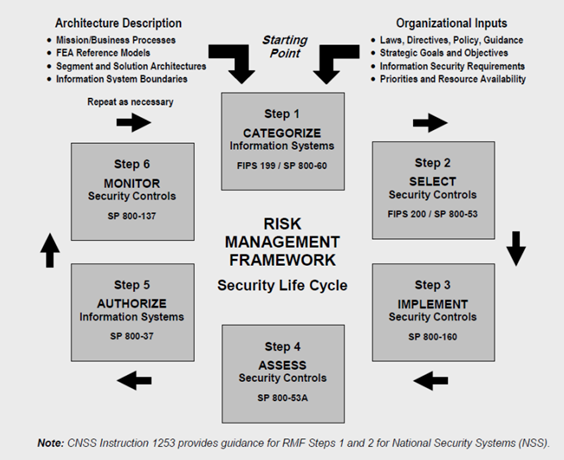
Example of a risk management framework (SP 800-53 Rev 4, page 8 (http://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-53r4.pdf))
To document its risk management framework, NIST produced multiple special publications. It includes the following components:
- Categorization (identification of risk level)
- Selection of security and privacy controls
- Implementation
- Assessment of the effectiveness of security controls
- Creating an improved system security profile, and what’s called an Authority to Operate (ATO)
- Monitoring and evaluating through iterations
The risk management framework helps put a security plan and guidance in a security context.
Was this article helpful?
Thanks for your feedback!

